Hello Vlad,
The mentioned task is quite simple if you define an advance routing rule with the action: Recipient > Recipient relay host = [<smtp_relay_ip>]
 Note the square brackets that will prevent any unneeded DNS lookups when you enter an IP address instead of a hostname.
Note the square brackets that will prevent any unneeded DNS lookups when you enter an IP address instead of a hostname.
*** Long post from here - please bear with me ***
Now, I have made some tests for your requested setup (with an Axigen standalone installation) and here are my comments:
1/ the best option is to configure DLP to send back the message via an authenticated SMP session.
There are several causes like: automatic disabling checks for SPF, DNSBL, etc
So, let’s say you will create a dedicate user for DLP service - in my example I assumed it is called dlp.user@domain.tld
2/ you have to configure the relay logic via advance routing rules and processing the DLP header via a sieve filter as only here we have access to header’s content.
Assuming that your DLP service is running an SMTP service at 192.168.100.10 let’s configure the SMTP part:
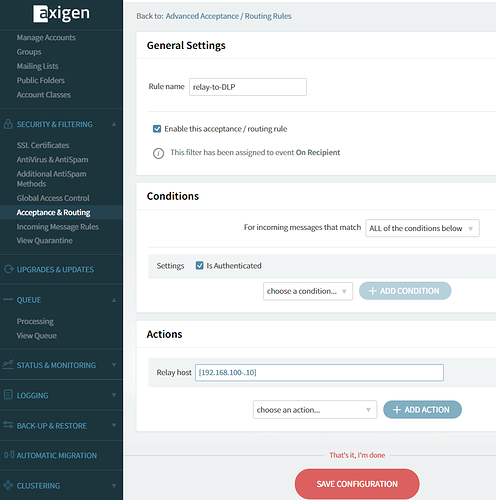
WebAdmin > Security & Filtering > Acceptance & Routing > Advance Settings > Add new rule
- name: relay-to-DLP
- conditions: all of the below
- Connection > Is authenticated > checked
- action: Recipient > Recipient relay host = [192.168.100.10]
- save configuration
Now, let’s made some manual changes to that rule in order to add some more conditions for the messages that should be relayed to the DLP service. For this please edit the filters/smtpFilters.script from Axigen working directory and identify + change the relay-to-DLP method like below:
method relay-to-DLP {
if (
allOf (
not (
is (authUser, "")
),
not (
isCase (mailFrom, "<>")
),
not (
is (authUser, "dlp.user@domain.tld")
)
)
) {
set (currentRcptRelayHost, "[192.168.100.10]");
}
}
After this change please restart Axigen service and from this moment all authenticated sessions that not belong to dlp.user@domain.tld will be routed to the DLP service, excluding the NDR messages that are send by will null sender.
Note: when manual changes are made into an advance routing rule please avoid further edits from WebAdmin as you will lose your previous changes
Let’s now continue with processing the header added by the DLP service. For this task please create a new file, called dlp.sieve, and place it in the filters sub-directory from Axigen working directory. The content of this file should be like:
require ["reject", "replace", "envelope", "vacation", "tagsubject", "body", "relational", "axidate", "addressbook", "restoremessage", "markmessage", "feature", "iConfirmation"];
##Filter id=11 name="DLP-BLOCK" enabled=1
if true {
if allof (
envelope :objecttype :contains ["From"] ["local"],
header :is ["X-RCIS-Action"] ["BLOCK"]
) {
reject "rejected by internal DLP policy";
stop;
}
}
##Filter id=12 name="DLP-QUAR" enabled=1
if true {
if allof (
envelope :objecttype :contains ["From"] ["local"],
header :is ["X-RCIS-Action"] ["QUAR"]
) {
quarantine "quarantined by internal DLP policy";
stop;
}
}
##Filter id=13 name="DLP-not-ALLOW" enabled=1
if true {
if allof (
envelope :objecttype :contains ["From"] ["local"],
header :contains ["X-RCIS-Action"] [""],
not header :is ["X-RCIS-Action"] ["ALLOW"]
) {
reject "unknown response from DLP service";
stop;
}
}
the scope being to take specific actions (reject or quarantine) only for messages sent by local hosted accounts.
After you create the new file please change the ownership to axigen user or double check that the mentioned user have read access to it.
In order to place this new sieve filter in the message processing flow please execute the following CLI commands:
config server
config filters
add scriptfilter name dlp file dlp.sieve
done
add ActiveFilter priority 10 filterName dlp filterType script
set applyOn (local relay)
done
commit
save config
quit
Just to be sure that the new filter is set correctly please check the output of the CLI list activefilters (from server-filters context) that should look similar with:
config server
config filters
list activefilters
The list of Active Filters:
priority | filterName | filterType
---------------------------------------
2 | AV:Tnef | socket
10 | dlp | script
195 | WASieveServer | script
My tests were made using Axigen WebMail interface and the flow was the expected one - in case this is not happening in your case or you like to made any changes please let us know (at one moment we may have to switch the discussion on the dedicated support channel but I’ll let you know if / when this is needed).
HTH,
Ioan
 Note the square brackets that will prevent any unneeded DNS lookups when you enter an IP address instead of a hostname.
Note the square brackets that will prevent any unneeded DNS lookups when you enter an IP address instead of a hostname.