Hello,
I have a problem with the SSL configuration.
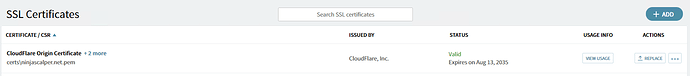
My certificate is already installed and valid. It is the same that is installed on my server for my website, so I can guarantee that it is working correctly:
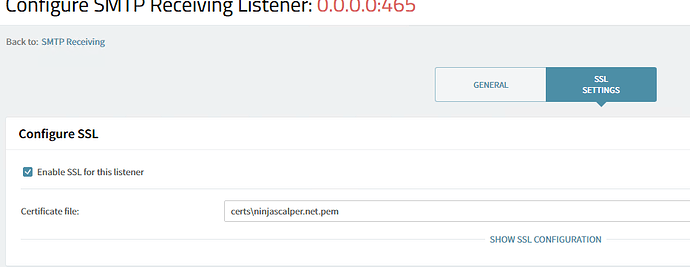
I chose the certificate on port 465:
But at the time of doing an email sending test I am not getting it.
The following logs appear:
2020-08-21 17:21:25 +0200 16 vps159681 SMTP-IN:00000000: << SSL: client hello, remote 151.80.130.233:59115, version TLS 1.3 (0304)
2020-08-21 17:21:25 +0200 16 vps159681 SMTP-IN:00000000: << SSL: client hello, remote 151.80.130.233:59115, session id 0df873a7f439f18032afb7c9e22a6efa4d91586d08309754077148c40897d063
2020-08-21 17:21:25 +0200 16 vps159681 SMTP-IN:00000000: << SSL: client hello, remote 151.80.130.233:59115, 75 cipher suites: 130213031301c02fc02bc030c02c009e00a200a3009fc027c023c013c009c028c024c014c00a006700330040006b00380039009c009dc0aec0acc0a2c09e0032c0a0c09c003c002fc0afc0adc0a3c09f006ac0a1c09d003d0035cca9cca8ccaac05dc061c057c053c05cc060c056c052c073c07700c400c3c072c07600be00bd0088008700450044c051c05000c000ba0084004100ff
2020-08-21 17:21:25 +0200 16 vps159681 SMTP-IN:00000000: << SSL: client hello, remote 151.80.130.233:59115, sni extension for mail.ninjascalper.net
2020-08-21 17:21:25 +0200 16 vps159681 SMTP-IN:00000000: >> SSL: server hello, remote 151.80.130.233:59115, version TLS 1.2 (0303)
2020-08-21 17:21:25 +0200 16 vps159681 SMTP-IN:00000000: >> SSL: server hello, remote 151.80.130.233:59115, cipher suite c02f
2020-08-21 17:21:25 +0200 16 vps159681 SMTP-IN:00000000: >> SSL: server write cert, remote 151.80.130.233:59115, version TLS 1.2 (0303)
2020-08-21 17:21:25 +0200 16 vps159681 SMTP-IN:00000000: >> SSL: server write cert, remote 151.80.130.233:59115, certificate 1: serial 60B32F8AFC1AADE55A80C5CC3A1A2D841599E5C5
2020-08-21 17:21:25 +0200 16 vps159681 SMTP-IN:00000000: >> SSL: server write cert, remote 151.80.130.233:59115, certificate 2: serial 0FEACE49D4C67C67
2020-08-21 17:21:27 +0200 02 vps159681 SMTP-IN:00000000: SSL alert remote 151.80.130.233:59115, undefined:fatal:certificate unknown
2020-08-21 17:21:27 +0200 02 vps159681 SERVER:00000000: SSL_accept error:14094416:SSL routines:ssl3_read_bytes:sslv3 alert certificate unknown
2020-08-21 17:21:39 +0200 08 vps159681 WEBADMIN:00009A04: previous line is repeated 4294967295 time.
2020-08-21 17:21:39 +0200 08 vps159681 WEBADMIN:00009A02: Session 0x93F0F5B7 associated with this connection
Am I doing something wrong? Is there a configuration missing?
Thanks