Basically I would like to transfer the Webmail access from port 80 to port 443 ( https:// ).
The procedure seems straightforward:
- create a Webmail Listener on the system’s IP, on port 443,
- upload certificate packages,
- enable the Listener.
The problem is that after days of searching and unsuccessful attempts it still not clear how to do this. Also, there is no clear and ‘always usable’ walkthrough in the knowledge base for this task.
In what form Axigen does like to see the certificates? How can one make sure that the uploaded files are correct (apart from the error message about wrong paths and certs)?
I have a bunch of files from the certificate authority, which I successfully use for a dozen websites of mine. Please help me use them for Axigen (if that’s possible)!
- There is .crt file, which is human readable and starts “-----BEGIN CERTIFICATE-----” and ends “-----END CERTIFICATE-----”
- I have a .csr file which I believe has no role here & now.
- There is the private key file .key which is human readable and starts “-----BEGIN RSA PRIVATE KEY-----” and ends “-----END RSA PRIVATE KEY-----”,
- I have a publik key which is human readable and starts “ssh-rsa…”.
- There are four other human readable files, two of them are the intermediate certificates and another two of them are the root certificates of the CA.
I tried the following:
-
Combined the .key and the .crt to a .pem using “cat”, uploaded, combined the intermediate certs to a .pem and uploaded them also. Chowned both files in the /certs directory with axigen:axigen. No joy, error message.
-
Converted the .key to a .pem using “openssl rsa…”, then combined it with the .crt using “cat”. Uploaded, chowned, still no joy.
-
Converted the .crt to .pem too, using “openssl x509…” then combined it with the .crt.pem using “cat”. Uploaded, chowned, still no joy.
How can one make this work?
Thanks in advance,
Peter
Hello Peter,
The solution is simple as follows:
- combine the .key and .crt to a .pem file and refer it in Certtificate file textbox
- combine the intermediate certificates to a .pem file and refer it in Certificate authorities file textbox
- enable SSL setting for this listener
- save settings
Note: for obvious reasons you have to keep the above files in a location where Axigen process could read them.
This is why, for example, you could keep them in the default working directory or under any other sub-directory (like certs), double checking that the file permissions allows axigen user to read them.
All should be fine now with your SSL listener (steps above are not specific only on the one for port 443).
In case you still have problems please attach a screen capture with your settings and the error you are receiving when enabling the SSL for that listener.
HTH,
Ioan
Hello Ioan,
thanks for the help. Still can’t do that, and I have no clue what I’m doing wrong.
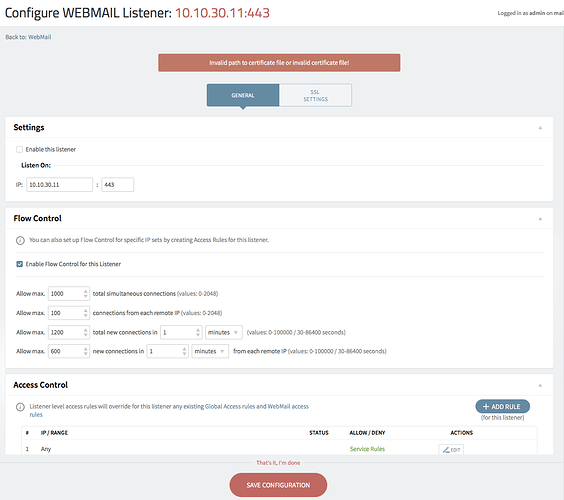
I can only post one image, which is the screenshot of the error message. Permissions are 777 for axigen:axigen for both the certificate.pem and the intermediates.pem.
The uploaded .pem files were made from the .crt and .key files with a simple ‘cat’ command.
Where is the mistake?
Kind regards,
Peter
Hello,
Could you please share your axigen.cfg file so I could check if there are any configuration errors inside it?
BR,
Ioan
Hello Ioan,
I’m not going to post our axigen.cfg on the forum. On the other hand, I can’t send a direct mail to you to ‘noreply’. Would you mind sending me a mail address I can reply to?
Kind regards,
Peter
Hello Peter,
OK - no problems.
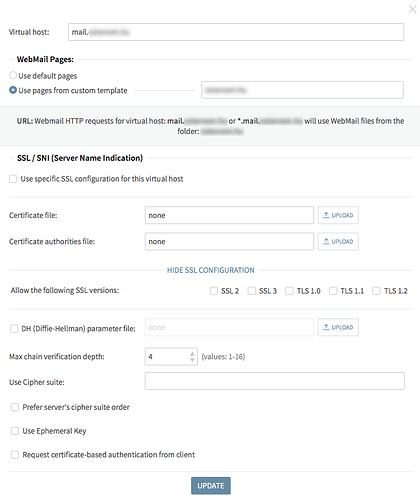
1/ Please double check if you have any virtual hosts that have enabled Use specific SSL configuration for this virtual host (WebAdmin > Services > WebMail > Virtual Hosts > Edit > SSL / SNI section).
If yes, please double check the files that are specified there as them are also verified when you are enabling the SSL WebMail listener
2/ Please provide more screen captures (for example you did not share the SSL settings for the listener you are trying to enable).
In other words help me to help you.
HTH,
Ioan
Hello Ioan,
thanks for your message. Please find the Virtual Hosts settings posted.
I believe the server is using the default Axigen cert for SMTP transactions. Can it be a problem, that for the Webmail I try to use our custom company cert? Do I need to use the same cert in both places?
Kind regards,
Peter
Hello Peter,
1/ So there are no virtual hosts in WebMail service that have SSL/SNI enabled - this is fine, so no possible errors here.
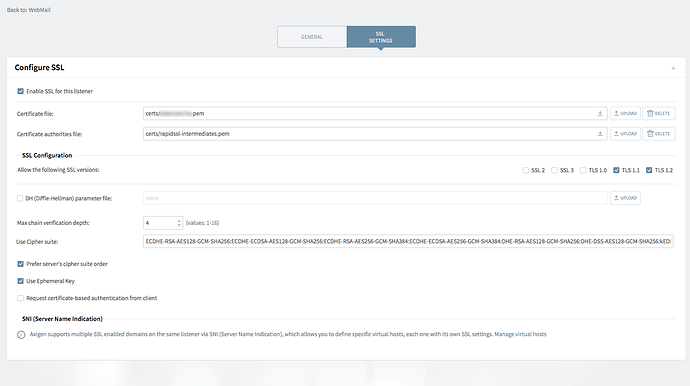
2/ Coming back to the WebMail listener on port 443 for which you could not enable SSL please share the SSL Settings of this listener as well.
3/ Regarding using different certificates for SMTP and WebMail there are no problems at all. More, you could use anytime different certificates on different listeners of the same service as well.
BR,
Ioan
Hello Ioan,
please see the SSL settings posted. Both certificates have permissions like axigen:axigen 777.
Kind regards,
Peter
Hello Peter,
Let’s validate your certificate file using openssl.
Assuming you have saved it in certs/my_domain.pem please issue the following commands and check if last 2 ones returns the same MD5 checksum.
# cd /var/opt/axigen
# openssl x509 -noout -modulus -in certs/my_domain.pem | openssl md5
# openssl rsa -noout -modulus -in certs/my_domain.pem | openssl md5
If not, or there are any errors than the .pem file is invalid (for example using not paired key and crt data).
Please advice.
BR,
Ioan
Hi Ioan,
thanks for your mail. Your last comment revealed the root cause of the whole error. The “cat” command concenates the input files, but that’s not good in case of the certificates, apparently.
“cat” makes a long string, and where the two certs meet, you will see this:
…Cav+FPg5eEveXTVyMnGo=
-----END CERTIFICATE----------BEGIN CERTIFICATE-----
MIIEszCCA5ugAwIB…
After editing the file with a word processor, and changing the string to this:
…Cav+FPg5eEveXTVyMnGo=
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIEszCCA5ugAwIB…
everything is working fine.
Thanks for the kind assistance, Ioan!
Regards,
Peter
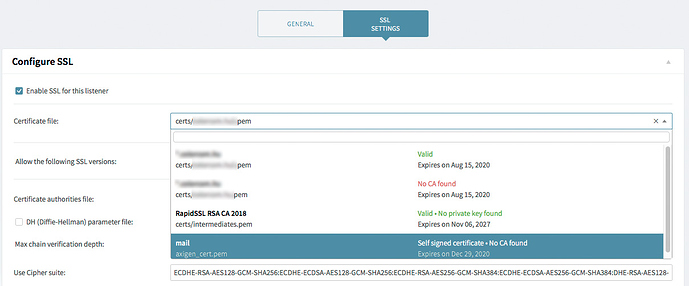
Just a follow-up for those who are not that strong on the SSL side, like me. In the latest Axigen incarnation (13) there is a nice feature which shows whether someone assembled the .pem file correctly or not.
If you copy all your assets into a pem file (any decent word processor or code writer app will do) it must be like this:
-----BEGIN RSA PRIVATE KEY-----
(Private Key: domain_name.key contents)
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
(Primary SSL certificate: domain_name.crt contents)
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
(Intermediate certificate: certChainCA.crt contents)
-----END CERTIFICATE----
Now copy that to your designated certificates storage directory in the system, and chown it for axigen. If everything is fine, you will see a green ‘Valid’ message when you check the cert in the pulldown menus.