Updated: April 2, 2025
Along with the ever-increasing number of cyber-attacks, organizations need to take measures to protect their assets. One of the tools they use are DMZs or Demilitarized Zone Networks.
In this article, we’ll share an overview of Demilitarized Zone Networks:
a. What DMZ Networks Are
b. The Benefits of DMZ Networks
c. How to Configure a DMZ Network
d. How to Harden the DMZ Network Servers
Let’s get into it.

What is a Demilitarized Zone Network?
In computer security, common setups used for small and medium networks include a firewall that processes all the requests from the internal network (LAN) to the Internet, and from the Internet to the LAN.
This firewall is the only protection the internal network has in these setups; it handles any NAT (Network Address Translation), by forwarding and filtering requests as it sees fit.
For small companies, this is usually a good setup. But for large corporations, putting all servers behind a firewall is not as effective.
That’s why perimeter security networks (also called demilitarized zone networks or DMZs) are used to separate the internal network from the outside world. This way, outsiders can access the public information in the DMZ, while the private, proprietary information is kept safely behind the DMZ, into the internal network.
This way, in case of a security breach, the attackers will only be able to access the servers in the DMZ network. This can be annoying and can lead to downtime, but at least the sensitive information is kept safe.
Here are a few examples of services that you can keep in the Demilitarized Zone Network:
- webservers with public information;
- the front-end of your application (the back-end should be kept safely behind the DMZ);
- mail servers;
- authentication services;
- services like HTTP for general public usage, secure SMTP, secure FTP, and secure Telnet;
- VoIP servers;
- VPN endpoints;
- application gateways;
- test and staging servers.
Why Use a Demilitarized Zone Network?
A DMZ server will secure your internal network from external access. It does so by isolating the public services (requiring any entity from the Internet to connect to your servers) from the local, private LAN machines in your network.
The most common method of implementing such a divider is by setting up a firewall with 3 network interfaces installed. The first one is used for the Internet connection, the second for the DMZ network, and the third for the private LAN.
Any inbound connections are automatically forwarded to the DMZ server because the private LAN doesn’t run any services and is not connectible. That’s how configuring a demilitarized zone network helps isolate the LAN from any Internet attacks.
How Do You Configure a Demilitarized Zone Network?
First of all, you need to decide what services will run on each machine. The DMZ server is usually on a different network segment, both physically and logically. This means that you need to use a separate machine to host the services you want to make public (such as DNS, web, mail, etc.).
From a connectivity point of view, the DMZ will be located on a different subnet than the LAN.
To build a Demilitarized Zone Network, you need a firewall with three network interfaces: one for untrusted networks (Internet), one for the DMZ, and one for the internal network. All servers you want to connect to the outside network you’ll put in the DMZ network, and all servers containing critical data you’ll put behind the firewall.
While configuring the firewall, you should put tight restrictions on the traffic towards your internal network, but you can be less restrictive with the traffic in your DMZ.
Next, you should provide NAT for the computers on the LAN in order to enable Internet access for the client hosts. You should also enable clients to connect to the servers in the DMZ.
Here’s a diagram of the final DMZ network architecture setup:
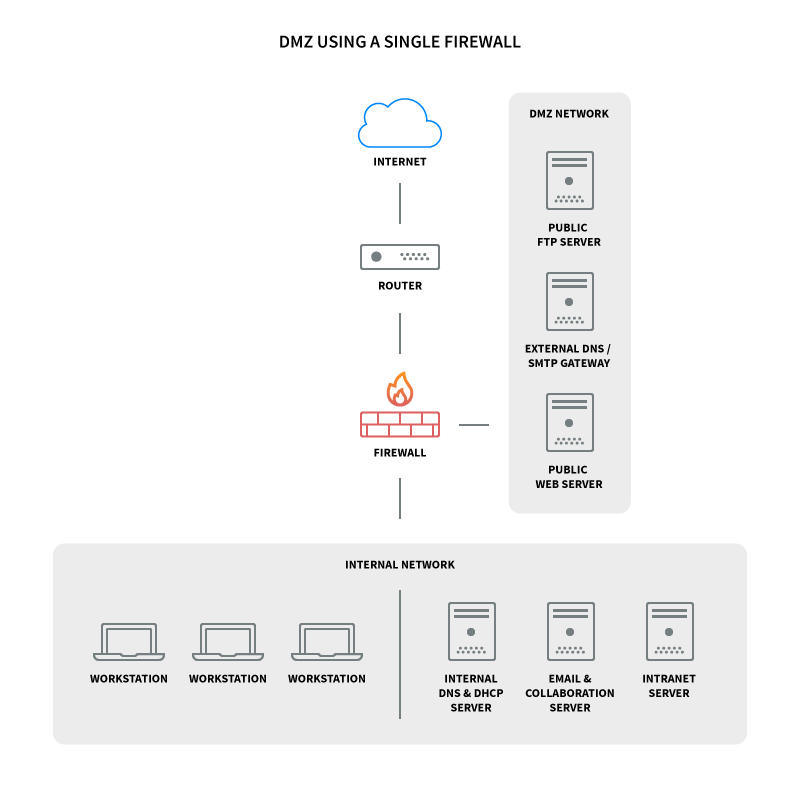
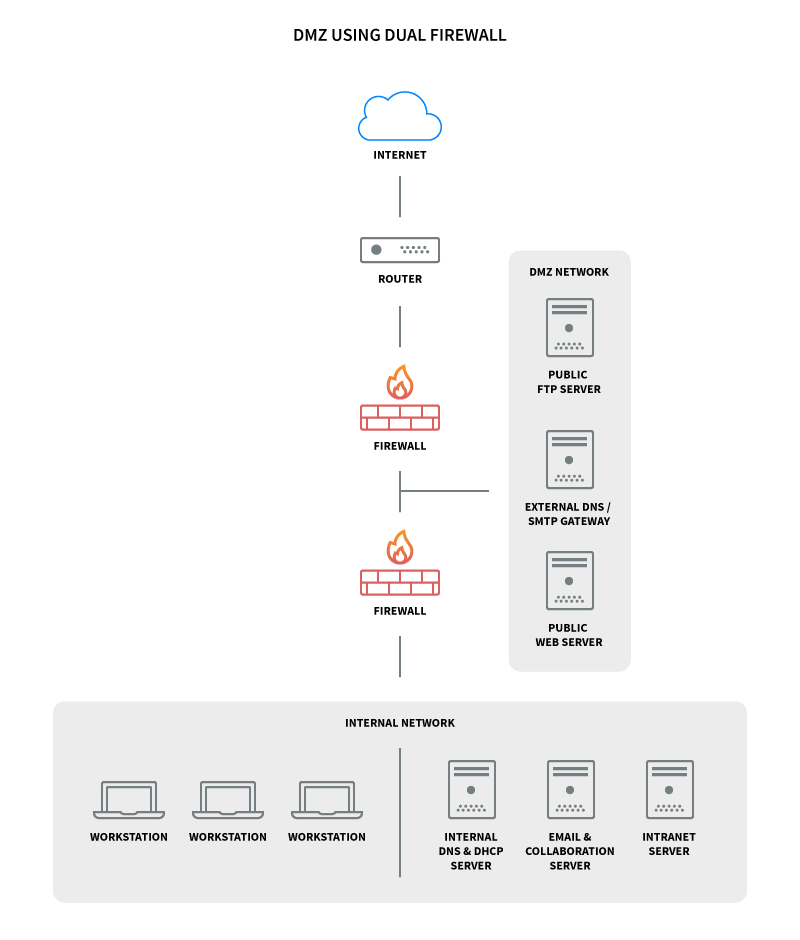
This configuration is also known as the three-legged model. To take network security up a notch, you can also use two firewalls (the back-to-back model). In this setup, one of the firewalls will allow traffic destined to the DMZ only, while the other only allows traffic to the DMZ from the internal network.
This provides an extra layer of security because two devices need to be compromised for an attacker to gain access to your internal network.
Here’s what a DMZ network diagram with two firewalls looks like:
Hardening the DMZ Servers
Computers in the Demilitarized Zone Network obviously need to be hardened as much as possible, given that they will be in the first line, right behind the firewall.
Their position will prevent attacks on the LAN, but it may also increase the risk of getting compromised.
Here are 6 ways to increase the security of your DMZ systems:
- Disable all unnecessary services and dæmons;
- Run services chrooted whenever possible;
- Run services with unprivileged UIDs and GIDs whenever possible;
- Delete or disable unnecessary user accounts;
- Configure logging and check logs regularly;
- Use your firewall’s security policy and anti-IP-spoofing features.
You can improve your DMZ infrastructure by adding multiple demilitarized zones with different security levels, depending on the number of systems and services being deployed. These zones can be assembled into a tier-like structure so that the information is passed from one DMZ server to another.
This type of network infrastructure may not be the most secure way of protecting the private perimeter, but it’s sometimes required.
An example of such a situation would be when a web server placed in a Demilitarized Zone Network requires access to a database server over a secured port (and that port only) placed in a second demilitarized zone network.
This database server could ultimately access some data found on the private LAN systems if there’s such a requirement. This way, the database is secured from public exposure, while keeping the webserver accessible and the private LAN, isolated.
Note: The above-listed methods apply to Linux / *NIX-type systems only.
What to Keep in Mind about DMZ Servers
The simplicity of the Demilitarized Zone Network concept makes it very powerful. That’s why we recommend you deploy your Axigen email server there instead of your internal network - to keep your email communication safe, as well as other sensitive data.
However, remember that a DMZ server can be considered a safe-guard, but is not a security measure by itself.
Still, with tight and well-thought network infrastructure, IDS (intrusion detection systems), and IPS (intrusion prevention systems), it can become a barricade against attackers and unwanted or unneeded traffic.