Picture this: you’re a service provider who receives a lawful intercept request.
You scramble to get everything ready in the short amount of time that you have to comply.
You must keep the customer safe and their email content gated and private.
There are too many steps to keep track of, not enough time, and so many rules to abide by. You’re feeling overwhelmed, and it’s clear that you should have been more prepared. Now you know.
This article helps prepare your service provider for lawful intercept by talking about the necessary internal processes, product requirements, and email requirements related to lawful intercept.
Here are some abbreviations to keep in mind throughout this article:
LI – Lawful interception
TC LI – Technical Committee Lawful Interception
CSP(s) – Communication Service Provider(s)
PTN – Public Telecom Network
CC – Contents of Communications
IRI – Intercept Related Information
LEMF – Law Enforcement Monitoring Facility (as defined by ETSI)
LEA(s) – Law Enforcement Agency(ies).

Lawful Interception — Short Review
Lawful interception (LI) is the legally grounded process in which a service provider or a network operator gives law enforcement agencies (LEAs) access to the communications of individuals or organizations. Communications can include video, voice communications, Internet connections, instant messaging, file transfers, data downloads, digital pictures, text messages, and others.
Lawful interception is crucial to preserving national security, combating crimes, and investigating serious criminal activities. You learned from our Lawful Interception for Service Providers article that communication service providers (CSPs) are required to comply with lawful intercept requests according to their local and national laws.
Internal Processes Necessary for Lawful Intercept
Unfortunately, LI is only straightforward by definition, not always in its application. That’s because what and how you need to support and fulfill the lawful intercept request depends upon:
- The government agency requesting the information
- Your role and liability in the delivery mechanism of the communication information
- The different LI regulations, based on the country and local, national, state-level, and federal laws, including laws at the EU-level
- The amount of time (depending on the country) you have to comply and respond to a LI request.
The standardization of lawful intercept is therefore vital to provide a technically and economically feasible solution that complies with national and international rules and regulations. ETSI has played a role in the standardization of lawful interception since 1991 and continues to this day, concentrated in the Technical Committee Lawful Interception (TC LI).
Their LI work covers every logistical aspect, from a logical overview of the entire architecture and the intercepted data flow, to the service-specific details of email and the Internet. For more info on their work supporting the international requirements of law enforcement agencies, you can find the current TC LI standards here.
Although the detailed requirements may differ from one jurisdiction to another, the general requirements stay the same. The lawful intercept system must provide transparent interception of only the specified subject or traffic, while the subject must not be aware of the interception. The service provided to other users must not be interrupted or affected during interception. Since the primary purpose of the service provider is to enable private communication between individuals, any LI functionality built into the network must not affect those individuals’ regular service. A service provider’s architecture requires a distinct separation between the Public Telecom Network (PTN) and the networks distributing and processing LI information.
Furthermore, LI deals with two types of information:
- Contents of Communications (CC) – the voice, video, or message contents
- Intercept Related Information (IRI) – the signaling information, the source and destination of the call, etc.
Product Requirements Necessary for Lawful Intercept
Alongside the types of information above, there are three primary requirements within the public telecom network to achieve LI. They are:
- Internal Intercept Functions (IIF) are located in the network nodes and are responsible for generating the CC and IRI.
- A Mediation Function (MF) delineates the PTN from the LEMF and communicates with the IIFs using Internal Network Interfaces (INI), which can be proprietary.
- An Administration Function (ADMF) handles serving interception orders and communicates with the IIFs and MF through an Internal Network Interface.
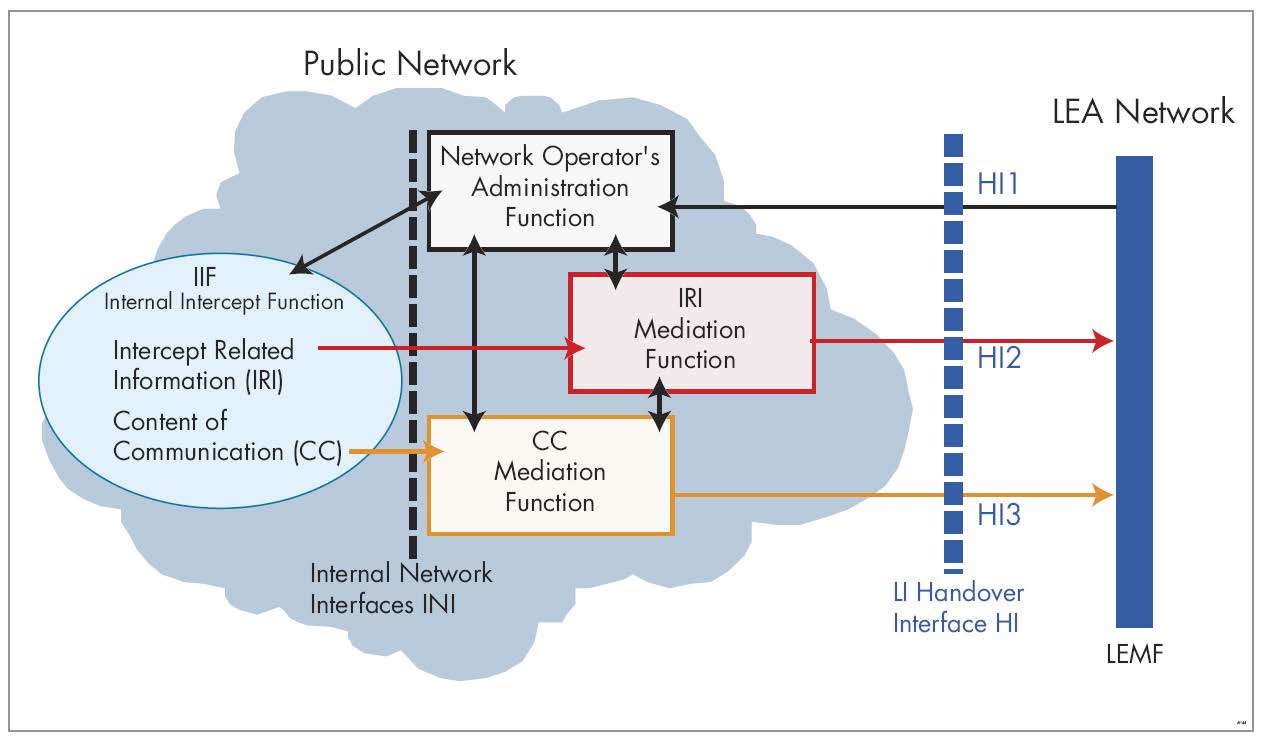
Although ETSI deals with the standardization of LI, from a CSP’s point of view, there is a lack of standardization across services and network equipment that can interfere with or make a smooth response with lawful intercept orders difficult. That’s because most service providers operate equipment from different generations of technology and can sometimes have different vendor environments as their networks transition from 2G to 3G to 4G and now to 5G. Not only that, but handover standards evolve over time, so older equipment or monitoring and analytics software can conform to only those older versions.
Challenges and Solutions For Lawful Intercept
Since communication patterns have changed, today’s lawbreakers have a wider range of sophisticated and encrypted communication channels available to them. Because of this, the scope of interception has also widened. The challenges facing some service providers are that they can’t meet the fundamental requirements of lawful interception without a dedicated LI solution.
A good LI solution from a service provider’s perspective will be cost-effective, have minimal impact on the network infrastructure, be compatible and compliant, support future technologies, and be reliable and secure. For different countries, there are different LI regulations, and most will deploy their own LI solutions. But in countries with emerging regulation, where the individual operators have yet to upgrade or build up their interception capabilities, an umbrella system works wonders. An umbrella system is a single, integrated LI system that covers all or several operators in a country.
For LEAs, the complexity of different handover versions creates insufficiencies and limits usability, especially when multiple carriers are involved in an investigation. There are ways around this, and they include:
- Simplify CSP operations – Operations teams at CSPs must routinely respond to lawful intercept orders by making the required modifications or configuration changes to network equipment.
- Prioritize and segregate intercepted data – A control structure must be in place to only allow access for authorized parties when an LEA requests lawful intercept data.
- Support any codec requirement – Sometimes, multiple LEAs may be involved in a lawful intercept order, some with complex requirements. Since audio coding for voice on equipment from various vendors might use a range of codecs, some equipment might not be compatible with that of LEAs’, often limited to support basic codec versions.
- Address any inconsistencies in handover data – Many LEAs have specific formatting requirements for handover data, and since a CSP is required to support many jurisdictions and agencies, the requirements for handover will become complex, costly, and require significant resources to support. Unless the data is scrubbed and normalized, mismatches in data encoding from different vendors interfere with LI orders.
Additionally, in these types of situations, an umbrella system works well again, taking any complexity away. CSPs and LEAs can treat intercepted data from all sources as a coherent whole, not having to take into account only specific functions.
There are numerous valid LI solutions on the market. The best way to introduce best practices for your service provider is to work with a solution vendor who has many years of experience in designing and implementing LI solutions. That means that the solution is compatible with as many network elements as possible and supports all standards. Regular updates and support must occur, as well as adaptations to any future requirements, so operators should consider the long-term investments. In other words, choose someone who will be there in the long run.
Email Requirements Related to Lawful Intercept
For any type of lawful intercept request, since you only have a specific amount of time to fulfill the request, it helps to be prepared. It will be challenging to comply if you’re not. For email access, the same rules apply across the board. Access to the email content (subject, body, attachments) must be kept private and gated by processes and access restrictions. Anyone other than the user is not allowed access to the email under normal circumstances. In the case of a valid lawful intercept request, the email’s content may be accessed by:
- the users themselves
- any other user who has access to the original user’s mailbox (sharing) - but this is ok because the user himself enabled sharing
- creating a copy of the message and storing it in a separate mailbox along with the original mailbox
- redirecting a copy of a certain user’s inbound and/or outbound messages to an external mailbox (can be an email address from the legal authorities)
- accessing a past backup and extracting the required email from there. If you have this capability, you should ensure that you don’t abuse this with the help of processes and access restrictions. Otherwise, you can be held liable for incorrectly attempting to access a user’s privacy. So it needs to be executed in accordance with the precise terms of a lawful intercept.
Go for Enhanced Security with Axigen
Thankfully, with Axigen, you have another solution to help with your preparedness for lawful intercept.
When talking about lawful interception, network security is one of the main concerns. We offer an extensive security toolset, with protection for your email traffic and extra security options that can be activated at your request. And regardless of which LI regulations you have in your respective countries, we will help you abide by them, including adherence to regulatory compliance requirements of major international standards.
Move securely forward, on your terms. Try Axigen today.