Safeguarding your customers’ information is essential to deliver optimized and business-aware products & services. In the following piece, we’ll talk from experience about how to protect customer privacy & gain their trust so they stick with you for decades to come.
While service/product quality & price still seem to be the greatest concerns for most consumers, it’s clear that we’re at the forefront of a paradigm shift towards more privacy. We at Axigen, as an email server software provider, know exactly what pain points end-users have in that area — so let’s dig in!
9 Easy Steps to Customer Data Protection that Anyone Can Take
A small note before we begin: in our honest opinion, when dealing with your customers, the point after this list — correctly communicating your commitment to customer privacy — is by far the most important, and you’ll see why. Yet, the work starts long before you get there:
1. Hire the Right People
The primary step is, of course, consolidating your team with customer cybersecurity representatives. So run to HR and set up a few job listings — if you don’t already have someone available for the job.
Cybersecurity Specialists handle most of the following things:
- providing security during dev stages
- look for hardware & software risks & vulnerabilities
- safeguard consumer data
- manage and monitor attacks
For more info on hiring a cybersecurity rep, check out this guide from LinkedIn.
Once you made the hire, put them to work as soon as possible. One cool approach that many medium & large businesses are taking is to have these reps “work for the consumers” — meaning they don’t have to beat around the bush to coddle company feelings. Since they work for the customer, their focus is on solving & preventing customer data privacy issues.
2. Understand Customer Privacy
Even though you have a person or team that safeguards consumer data privacy, it might be insufficient. You have to train them on how important customer privacy is.
Not only that, but executives & other managers in your business should take part — yes, that means you too! Furthermore, make those training materials mandatory reading for anyone even remotely dealing with customer data.
Here’s a sample of the most important places to look:
- Coursera has a wealth of courses dealing with customer privacy & data protection, data protection in the cloud, and so on.
- The Data Privacy Strategy Cornell Certificate Program at Cornell University is extremely useful and completely online
- The Certified Information Privacy Professional (CIPP)l Program from the International Association of Privacy Professionals (IAPP) is the most renowned certification program in the Privacy sector. They also offer programs dedicated to certifying entire enterprise teams — so if you want to send more people to this type of training, this might be your best bet.
Even if you somehow managed to skip this step and implement proper security measures, your messaging might appear entirely tone-deaf, and that’s a PR crisis waiting to happen. Big tech is constantly in the headlines with similar issues: think of a big company that starts with ‘F’ and ends with ‘k’ & you’ll get it. PR issues can become very costly, mostly because of damage control efforts that might sink you deeper instead of saving you. This is a good point you can make for ROI of cybersecurity, more of them down at point 9.
Collect Only What You Need
As part of the first cybersecurity audit you do, you must establish precisely:
- what customer data you’re collecting
- what customer data is necessary to run your business
- what customer data is optional & good to have
- what customer data you should be collecting
Once you have clear-cut lists for all of those, you need to do the important job of deciding how to collect that data in a customer-centric & empathy-driven approach. It’s not easy — you’re going to have to ask tough questions: do you need more than names & emails? Do you have a secure system in place to collect credit card info?
Then comes another important question: what customer data do you store, where do you store it, and for how long? Do you (need to) keep data that’s automatically collected through your client? It depends. Are you allowed to? Again — it depends.
We recommend reaching out to a lawyer to discuss your concerns. The questions will multiply, get longer & more complex depending on your type of business. But this is a good starting point.
4. Implement Cohesive Security Measures
Once you have all the basics covered, you’re going to have to go into niche-specific security measures. This largely depends on your business.
We at Axigen, as a mail server software company, have multiple security layers in place to protect our customers and our customers’ customers:
- Multi-layer access control. Designed to stop DDoS attacks and prevent spammers from reaching users.
- Flow control. A system that prevents too many simultaneous connections, with complete control for users to configure their own services.
- Many more security measures: sender validation, greylisting, Message integrity validation, blacklisting / whitelisting, country filtering, DNS Checks, antivirus filtering, and many, many more, which you can read about on our mail server security page.
Important: consider geo-specific security measures. Things like the many minor, federal and state-level laws in the US or GDPR in the EU might significantly change your approach to customer privacy protection.
Do All the Updates (Almost)
Updates make the digital world go round. If you’re a security person, you know precisely why updates are essential — unless they’re not. In most cases, you should do all the updates as soon as they come out and encourage your users to do the same. From Windows to all the other software you or your customers might use.
Data breaches sometimes occur in the weirdest of places, so having the latest security updates is often more important than users think. To get a sense of how this might work, let’s look at an example:
In July 2015, hackers managed to get control of some Jeep vehicles by simply using Sprint as their carrier & connecting to the cars. This was a clear example of Jeep overlooking security updates.
However, this example is also a good cautionary tale for doing too many updates. Jeep users that hadn’t installed the latest firmware update were safe from the attacks. One approach we recommend here is Googling any major update before proceeding with it. If there are big issues with it, there will usually be a Reddit thread about it.
6. Secure Authentication
One of the most vulnerable parts of any software solution is the authentication stage. Simply having two-factor authentication is a primary step to secure the login process.
However, here you’ll bump into a different security concern: collecting even more data. So balance is key, and communicating openly is vital — after all, sharing your phone number can be extremely dangerous.
Here at Axigen, we use CRAM-MD5, LOGIN, PLAIN, DIGEST-MD5, and GSSAPI methods (in this order) for client authentication. Read more about Axigen authentication & encryption here.
7. Secure the Cloud
If you’re using the cloud for any part of your business or any services you provide, good job! Cloud-native has incredible business benefits. It’s the future and we firmly believe that here at Axigen.
Switching to a cloud-native infrastructure should be the focus of IT leaders. They must develop a decision framework to systematically examine use-case scenarios for adopting cloud computing. And correlate that with the enterprise architecture of the business they support. Such a framework forms the backbone of any successful cloud strategy.
CEO, Axigen — during CloudFest 2021
However, the cloud-native approach comes with many industry-specific and provider-specific security concerns. And if you don’t want to become the next Apple iCloud, you need to take the necessary steps to secure any part of your business that touches the cloud.
8. Make Customer Privacy Protection a Core Value
If you’re in a business that has many touchpoints with its customers’ data, prioritizing customer privacy protection might not be enough. The same applies if your customers’ data is particularly sensitive.
We recommend going so far as making protecting customer privacy a core value of your enterprise. It’s just a way to make sure it stays top of mind throughout your organization. However, core values tend to be taken less seriously the bigger a business becomes — so proactively plan for that.
9. Understand the ROI & Communicate It
In today’s world, consumer privacy is government-mandated in most regions & countries (unless you’re in the United States where the FCC has yet to offer clear guidelines on it and has left it up to the State Governments, for the most part). As such, the ROI of basic efforts to protect personal consumer data is clear.
However, you need to go deeper:
Executives throughout your organization need to understand the ROI of spending more on cybersecurity. It’s especially challenging to drive the point home for small businesses, but we believe it’s better to tackle cybersecurity concerns before they become cybersecurity problems.
The ROI is simple: if there are no issues, there are no reasons for users to go to customer support, if there are no reasons for people to go to customer support, then they will stick around for a lot. Surveys show that poor customer support is the no.1 reason people switch providers.
Communicate Your Commitment to Customer Privacy
Of course, this isn’t as important as doing the work - after all, you shouldn’t lie. But your focus as a business from a communication perspective should be easing feelings of anxiety. And when it comes to personal data security, that anxiety can be very, very high.
A 2019 study by Pew Research showed that Americans are “concerned, confused, and feeling lack of control over their personal information” — and think about it, that was before the pandemic & the age of remote work.
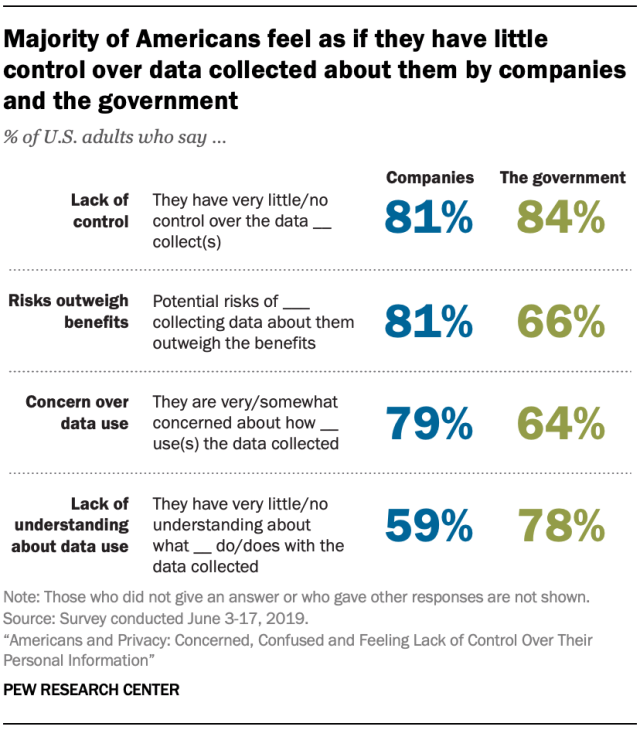
Image source: Pew Research Study on “Americans and Privacy.”
So align your messaging. Make sure you’re saying the right words at the right time:
- be understanding
- be empathetic
- address concerns head-on
- be as transparent as possible in your approach
Being direct when addressing privacy concerns promotes trust and heavily influences customer stickiness. In a 2019 Tripwire survey, 57% of Infosecurity professionals admitted they stopped using a B2B product because of security vulnerabilities. So even the slightest concern about cybersecurity weak spots can lead customers away.
Bottom Line
These steps for how to protect customer privacy and secure trust should be mandatory for any business. Go through these steps in a data-driven approach with contingency plans for any customer privacy risks, sorted by the seriousness of the potential impact.
And of course, if you’re looking for a 100% secure business mail server solution, look no further than Axigen. We hope this article has been illuminating & we’ll check back with you all in the next one!