- Axigen 'opt' Directory
- Axigen Working Directory
- The mqview Tool
- A-grade SSL Listeners
- Configuring the WebMail & WebAdmin Discovery by Search Engines
- Sender Rewriting Scheme (SRS)
- Configuring the WebAdmin Customer Reference as Read Only
- Securing SMTP Services
- Additional Fine-Tuning via Environment Variables
Updated: September 21, 2021
The following page will show you how to enable advanced configuration settings within the Axigen WebAdmin in order to secure SMTP Receiving services.
We recommend the following settings:
-
define two listeners (one listening on port 25 and one on 587)
-
(optionally — but recommended) define one listener on 465
-
Configure on both listeners the SSL details for enabling
STARTTLS -
disable authentication on plain text connections
-
enable authentication on secure connections (only after
STARTTLS)
What Are the 3 Different Ports (25, 465, and 587) for SMTP Receiving Services?
The 3 different SMTP ports are officially labeled as follows:
-
25 - SMTP — used by MTA to MTA communication (mail server to mail server). It may be used for client to server communication but it is not currently the most recommended
-
465 - SMTPS — SSL encryption is started automatically before any SMTP level communication
-
587 - MSA — almost like standard SMTP port. SSL encryption may be started by the
STARTTLScommand at SMTP level if your ISP does not modify / filter server'sEHLOreply. Since several ISPs block outgoing connections to port 25, an Axigen server should allow port 587 incoming in order for the mobile users to be able to submit messages.
The STARTTLS ESMTP Extension for Incoming SMTP Connections
Check that the STARTTLS ESMTP extension is enabled for incoming connections (use of this extension is up to the remote MTA or Client):
-
Go to WebAdmin → Security and Filtering
-
Click on Acceptance and Routing
-
In the Acceptance Basic Settings check the Allowed ESMTP Commands
-
Make sure that the "Allow StartTLS" checkbox is ticked
The STARTTLS ESMTP Extension for Outgoing SMTP Connections
Check that the STARTTLS ESMTP extension is enabled for outgoing connections (if the remote MTA server that Axigen is relaying an email to will advertise that it supports STARTTLS then Axigen will obey this configuration):
-
Go to WebAdmin → Security and Filtering
-
Click on Acceptance and Routing
-
In the Routing Basic Settings check the Outgoing delivery settings
-
Make sure that the "Use StartTLS" checkbox is ticked
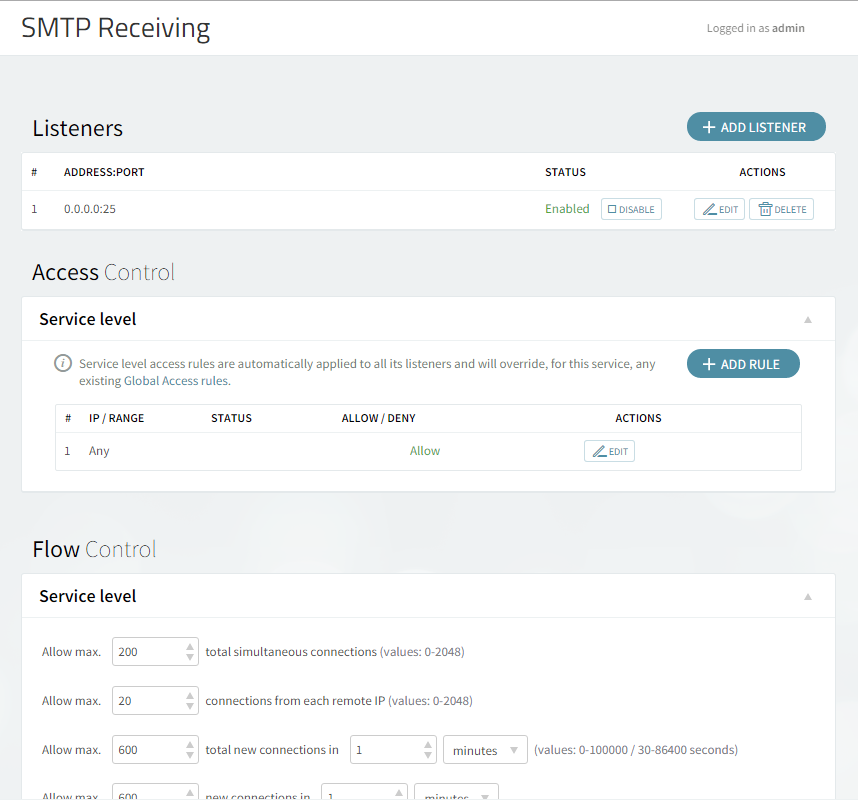
How to Configure the SMTP Listeners
SMTP Ports: 25 and 587
These two ports should permit non SSL connections but should allow the STARTTLS ESMTP extension
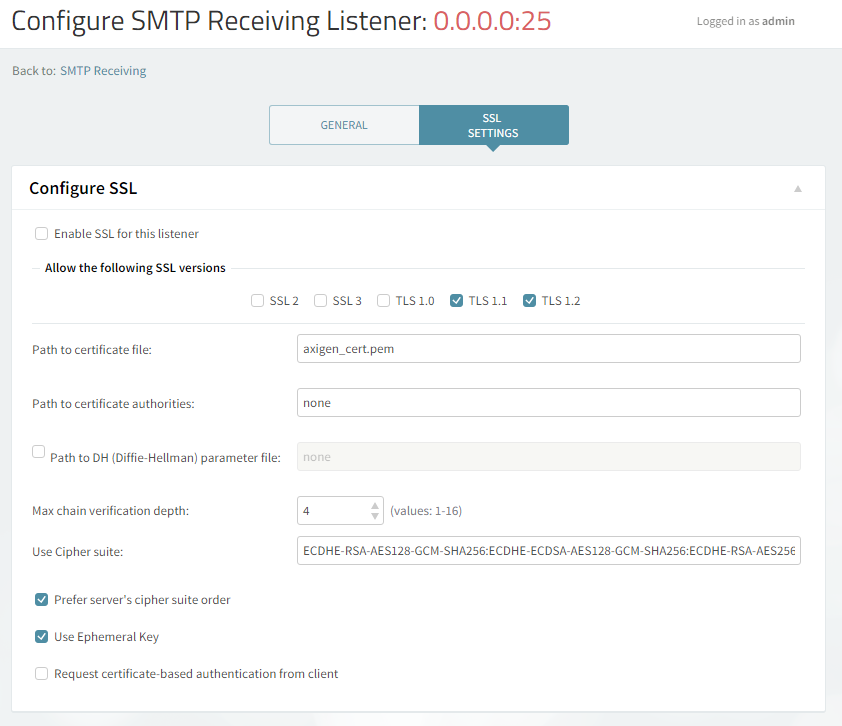
The SSL Settings tab on the Listener's configuration should be the same on both these listeners:
Please note the following:
-
The "Enable SSL" checkbox should not be ticked for this listener since these two listeners should accept non SSL connections and only start SSL when the SMTP protocol command
STARTTLSis issued by the client -
The SSLv2 and SSLv3 are disable since these two old SSL protocols have a well known set of vulnerabilities
-
In case you choose to use DHE ciphers (e.g.
DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA) you have to configure a Path to DH (Diffie-Hellman) parameter file
SMTP Port: 465
The 465 port should permit only SSL connections.
In order to achieve that, the checkbox "Enable SSL" should be ticked for this listener.
How to Change the Rules for Authentication
Disabling authentication on plain text connections and enabling authentication on secure connections (only after STARTTLS) is accomplished in Axigen by means of the Advanced Acceptance / Routing Rules (which can be configured from WebAdmin → Security and Filtering → Acceptance and Routing → Advanced Settings).
Two rules have to be defined:
-
disableAUTH_on_non_SSL
-
enableAUTH_on_SSL
Disabling Authentication on Plain Text Connections
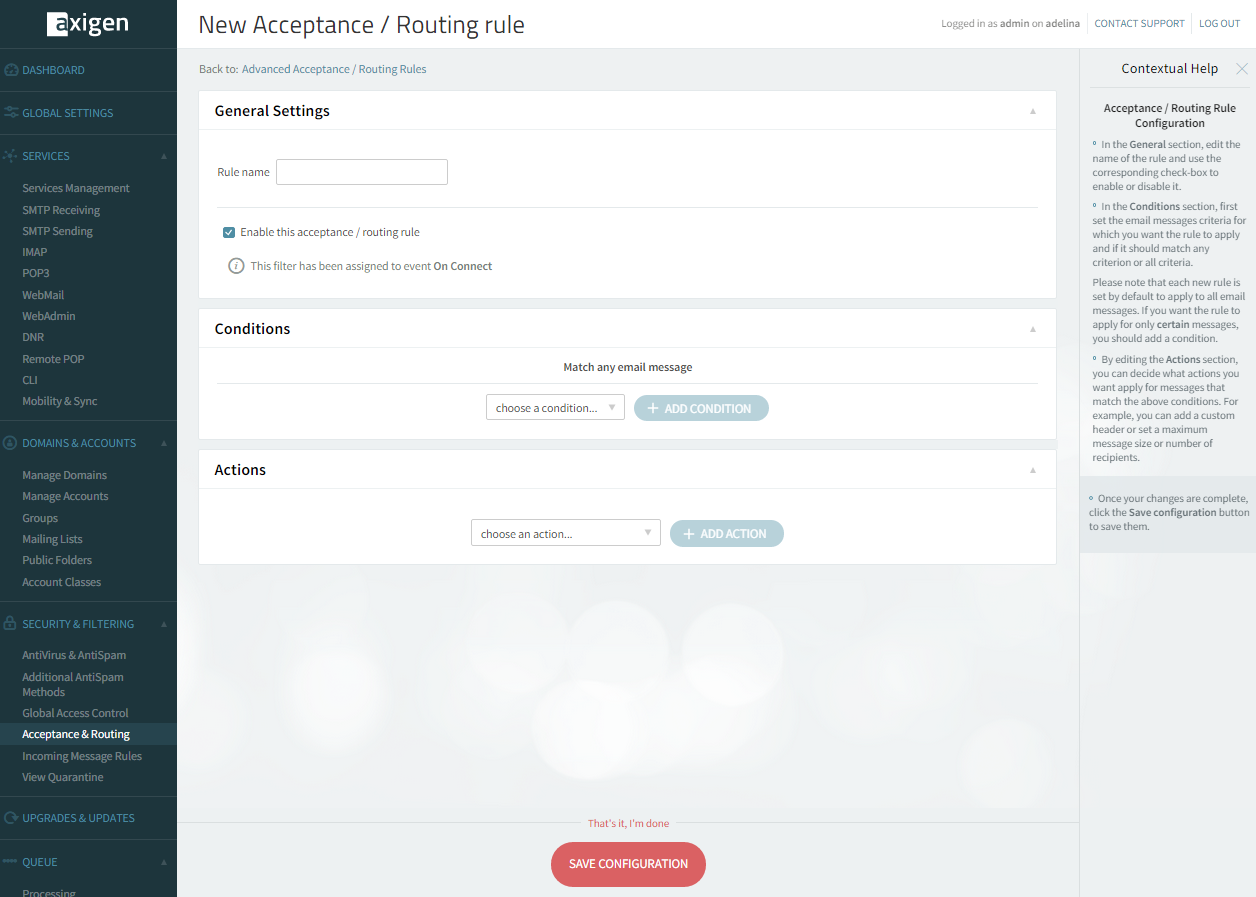
-
Click on "+ Add Acceptance / Routing Rule".
-
In Rule Name enter "disableAUTH_on_non_SSL" (or choose another name)
-
In Conditions leave empty. This would mean that the rule will match any email message
-
In Actions choose the action"Plain connections authentication" and set "Not authenticated"
-
Click Save Configuration
Enabling Authentication on Secure Connections (only after STARTTLS)
-
Click on "+ Add Acceptance / Routing Rule".
-
In Rule Name enter "enableAUTH_on_SSL" (or choose another name)
-
In Conditions leave empty. This would mean that the rule will match any email message
-
In Actions choose the action"SSL connections authentication", set "Authenticated" and check what authentication mechanisms you want. Since this is on a secured session, you can leave the Plain and Login authentication mechanisms on without any worry.
-
Click Save Configuration
Order of Rules
In the Advanced Acceptance / Routing Rules screen, make sure that the disableAUTH_on_non_SSL rule precedes the enableAUTH_on_SSL one.
How to Require STARTTLS for Incoming SMTP Connections to a Certain Domain
In order to force the use of STARTTLS for either incoming or outgoing SMTP connections, a new Acceptance and Routing Rule has to be defined.
This is especially useful when:
-
you want to accept emails for a local domain only if the remote servers uses
STARTTLS
The following rule has to be defined:
-
Click on "+ Add Acceptance / Routing Rule".
-
In Rule Name enter "allow_only_tls_for_mydomain_com" (or choose another name)
-
Select the condition "Connection → isSSL" and leave the checkbox unticked
-
Select the condition Recipient → Domain is "mydomain.com" → replace with your own domain name for incoming or external domain name for outgoing
-
Change the dropdown For incoming messages that match and choose ALL.
-
Add action "SMTP → Action”, choose Reject in the dropdown, and write an explanation like: "Accepting only secure delivery (STARTTLS) for mydomain.com".
-
Click Save
Forcing Outbound SMTP Delivery Only Using SSL with TLS1.1 and TLS1.2 for a Specific Domain
The SSL Settings tab on the Listener's configuration should be the same on both these listeners.
In case you want to make sure that your Axigen server will ONLY deliver email to other email servers out there using STARTTLS using only TLS1.1 and TLS1.2, the following rule has to be defined:
-
Click on "+ Add Acceptance / Routing Rule".
-
In Rule Name enter "use_only_tls11_and_12_when_relaying" (or choose another name)
-
Select the condition Delivery → Relaying mail
-
Select the condition Recipient → Domain is 'example.com'
-
Change the dropdown “For incoming messages that match” and choose “ALL”.
-
Add action Relay → Host and populate the smart host for this domain and the SSL remote enabled port
-
Add action Relay → SSL Encryption and make sure the checkbox is checked
-
Add action Relay → SSL Versions and make sure only TLS1.1 and TLS1.2 are checked
-
Click Save