The Axigen mail server provides routing options at SMTP In, POP3 Proxy and IMAP Proxy level through its integration with OpenLDAP. LDAP stands for Lightweight Directory Access Protocol. It is a model for Directory Services that provides a data/namespace model for both the directory and a specific protocol.
A directory is a specialized database with a hierarchical structure designed for frequent queries but infrequent updates. Unlike general databases, they don't contain transaction support or roll-back functionality. Directories are easily replicated to increase availability and reliability.
In order to be configured for use within Axigen, OpenLDAP has to already be set up. OpenLDAP installations may very, depending on your preferred operating system. Integrating OpenLDAP with Axigen is a two-step process, as described below:
1. Configuring OpenLDAP for Axigen
The localdomain.test address is used as an example. Please remember to edit it accordingly.
-
please run the following command and then place the following text:
-
In order to add users to the LDAP directory, add the following into a file. You may add as many users as you want in this file:
-
Then run the following command:
-
You will be asked for the password you set up in the /etc/openldap/slapd.conf file (in our example, "secret").
-
You can test if the user was added using the following command (the second version of the command includes authentication:
-
In order to delete an entry, use the command:
-
To edit an LDAP entry, just use:
Note that you must press another <Enter> after the modified field.
2. Configuring LDAP connectors in Axigen
The LDAP connector can be configured via Webadmin -> "Clustering" -> "Clustering Setup" -> "LDAP Connectors" tab -> "Connector List" section -> press the "Add Connector" button.
The connector options should be entered based on the settings of your LDAP server. Enter a name for the connector in the "LDAP Connector name" field.
In the "LDAP Server Parameters" enter:
-
the IP/Hostname and Port on wich the LDAP server is listening. By default the port is 389;
-
from the "Server type" drop-down box select the server type you wish to use the connector with: OpenLDAP or ActiveDirectory;
-
if you are setting up the Axigen server for a cluster environment check the box related to the "Enable Clustered Operations" option, which when enabled will determine Axigen to match entries based on the backend hostname attribute).
If you enable this option in an Axigen to LDAP synchronization process, Axigen will add the mailHost parameter to Axigen accounts synchronized with the LDAP server. For the mailHost parameter Axigen will use the value set in WebAdmin -> "Global Settings" -> "General" section -> "Server name". By default this is the station hostname on which Axigen is installed.
-
in this section you can also set the "Timeout" counter (interval corresponding to the timeout on an Axigen <-> LDAP connection) which is by default set to 4 seconds and can take values between 1-600 seconds, the "Polling interval" (time period between two automatic Axigen to LDAP queries) which is by default set to 10 seconds and can take values between 2-600 seconds and "Transient error retry interval" counter which is by default set to 5 seconds and can take values between 2-600 seconds.
-
select the required synchronization method from the drop-down box related to the "Synchronization direction" entry. You can choose to use Axigen to LDAP, LDAP to Axigen or Both ways. If you choose both ways synchronization you will then have to choose a winner for the situations when there is a parameter synchronization conflict (LDAP and Axigen have a different value for a parameter).
In the "LDAP Search Parameters" you can set:
-
enable the "Use Administrative DN" - This option instructs Axigen to authenticate, using the defined user, to the LDAP server before requesting information. This user is the admin user defined in the LDAP rootdn configuration;
-
enter the proper "Admin DN" and "Admin DN Password";
-
in the "Account base DN" field enter the DN of the LDAP organizational unit where the user accounts are defined. For example: ou=Users,dc=example,dc=test. You can also use the %x parameter, to create a connector that can be used in a multiple domain setup, which will expand depending on the name of the synchronized domain.
if you wish to also synchronize the Axigen Groups with the LDAP server, you can optionally check the box related to "Enable Group Synchronization" and enter in the "Group base DN" field the DN of the LDAP organizational unit where the group accounts are defined. For example: ou=Groups,dc=example,dc=test.
-
if you wish to use a custom correspondence between the Axigen account parameters and the LDAP parameters, you can check the box related to the "Use custom schema" option. Then enter the custom schema file name in the related text box. To obtain a custom schema for your setup, please contact our support line, making sure you provide them with your requirements and examples of what custom account parameters you wish to use.
In the "LDAP Routing Configuration" section you can set the "Hostname attribute" which has to point to the LDAP account parameter that holds the hostname of the server where the account is located (ex: mailHost). This parameter is used by Axigen when you configure SMTP or WebMail/IMAP/POP3 proxy routing, to determine to which server it will route the respective connection. This is useful in a clustered environment.
Configuring mapping parameters
In order to successfully route connection on either of the supported protocols, SMTP, POP or IMAP, you need to set mapping parameters. The easiest and most intuitive way of setting mapping parameters is through WebAdmin, Axigen's web-based administration interface.
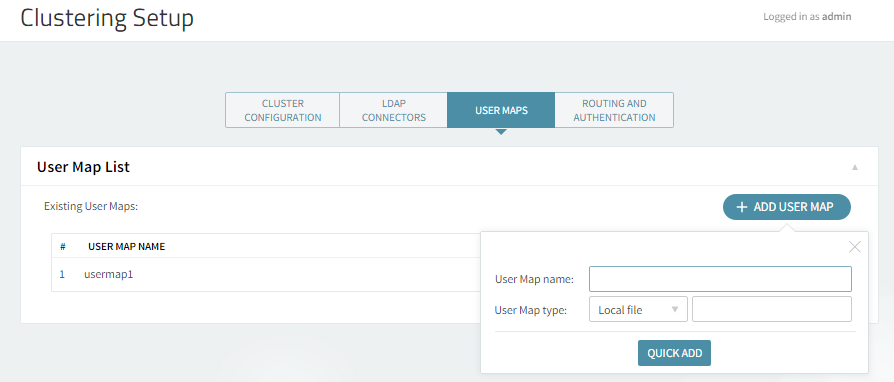
In the User Maps page you can add and configure a list of User Maps at server level. In order to do so, you should access "Clustering" -> "Clustering Setup" -> "User Maps" page and hit the "Add User Map" button.
For each new user map, the following parameters are available: name, type (Local file, LDAP Password, LDAP Bind) and, as the case may be , either file location or defined LDAP Connectors.
POP3 Proxy service
The Axigen POP3 Proxy module establishes connection trough remote servers with POP3 clients. The server accepts connections as specified by the POP3 Proxy listeners defined in the configuration file. By default the server accepts connections on 127.0.0.1:110 .
Listeners
Listeners can be defined and managed to add extra flexibility and configurability to this service. For that, global access limitations, SSL Settings and access lists can be enforced on the address used by this service for binding.
Access control
Access rules allow you to control connection to this service by defining simple access lists for specific Networks / IP Ranges / IP’s. Service level access rules are automatically applied to all its listeners and will override for this service any existing Global Access rules.
Flow control
Flow control parameters can be adjusted to fine tune the server’s performance and avoid overloading it. Global access limitations to this listener can be enforced by setting the total number of simultaneous connections, concurrent connections from each remote IP address, number of new connections to the listener made in a time period interval, number of total connections from each remote IP address on a time interval period. The default interval for this time period is set to 1 minute.
Logging
All Axigen main services can log different types of events. You can specify what events are logged, where and how they are logged.
Encryption and authentication
The POP3 Proxy service only supports PLAIN authentication, which is why it is recommended that StartTLS or SSL are used for encrypting the connection. The authentication can be performed on the POP3 proxy or on the back end server.
Error control
To protect the server, the number of failed / wrong commands received from POP3 clients during one session can be limited. When these limits are exceeded, incomplete connections or connections that are not RFC compliant will be dropped thus freeing important bandwidth.
If you do not specify a limit for the maximum number of (authentication) errors allowed for a POP3 client's session, security risks may arise.
Thread management
The Axigen mail server is designed to run on different machine configurations and operating systems, on networks with various traffic loads, structures, domain configurations, user rights etc. That is why, depending on all these variables, you can adapt the workload to the server’s processing power to improve its performance or avoid overload by setting the minimum and maximum number of threads that can be opened at a specific moment of time.
Back-end server connection settings
In this section, you can allow a connection timeout to be set, specify the maximum number of connections between POP3 Proxy and the back-end Server, another local network interface IP address to be used for connections with the back-end server and whether or not to use SSL to connect to the back-end server.
IMAP Proxy service
The Axigen IMAP Proxy module establishes connection trough remote servers with IMAP clients. The server accepts connections as specified by the IMAP Proxy listeners defined in the configuration file. By default the server accepts connections on 127.0.0.1:110 .
Listeners
Listeners can be defined and managed to add extra flexibility and configurability to this service. For that, global access limitations, SSL Settings and access lists can be enforced on the address used by this service for binding.
Access control
Access rules allow you to control connection to this service by defining simple access lists for specific Networks / IP Ranges / IP’s. Service level access rules are automatically applied to all its listeners and will override for this service any existing Global Access rules.
Flow control
Flow control parameters can be adjusted to fine tune the server’s performance and avoid overloading it. Global access limitations to this listener can be enforced by setting the total number of simultaneous connections, concurrent connections from each remote IP address, number of new connections to the listener made in a time period interval, number of total connections from each remote IP address on a time interval period. The default interval for this time period is set to 1 minute.
Logging
All Axigen main services can log different types of events. You can specify what events are logged, where and how they are logged.
Encryption and authentication
The IMAP Proxy service only supports PLAIN authentication, which is why it is recommended that StartTLS or SSL are used for encrypting the connection. The authentication can be performed on the IMAP proxy or on the back end server.
Error control
To protect the server the number of failed/wrong commands, received from POP3 clients during one session, can be limited. When these limits are exceeded, incomplete connections or connections that are not RFC compliant will be dropped thus freeing important bandwidth.
If you do not specify a limit for the maximum number of (authentication) errors allowed for a POP3 client's session, security risks may arise.
Thread management
The Axigen mail server is designed to run on different machine configurations and operating systems, on networks with various traffic loads, structures, domain configurations, user rights etc. That is why, depending on all these variables, you can adapt the workload to the server’s processing power to improve its performance or avoid overload by setting the minimum and maximum number of threads that can be opened at a specific moment of time.
Back-end server connection settings
In this section, you can allow a connection timeout to be set, specify the maximum number of connections between IMAP Proxy and the back-end server, another local network interface IP address to be used for connections with the back-end server and whether or not to use SSL to connect to the back-end server.
WebMail Proxy service
The Axigen WebMail Proxy is an Axigen service (somewhat similar in functionality and configuration with the IMAP Proxy and POP3 Proxy services) that allows connection proxy-ing from the front-end layer to the back-end layer in a clustered environment.
Listeners
Listeners can be defined and managed to add extra flexibility and configurability to this service. For that, global access limitations, SSL Settings and access lists can be enforced on the address used by this service for binding.
Access control
Access rules allow you to control connection to this service by defining simple access lists for specific Networks / IP Ranges / IP’s. Service level access rules are automatically applied to all its listeners and will override for this service any existing Global Access rules.
Flow control
Flow control parameters can be adjusted to fine tune the server’s performance and avoid overloading it. Global access limitations to this listener can be enforced by setting the total number of simultaneous connections, concurrent connections from each remote IP address, number of new connections to the listener made in a time period interval, number of total connections from each remote IP address on a time interval period. The default interval for this time period is set to 1 minute.
Logging
All Axigen main services can log different types of events. You can specify what events are logged, where and how they are logged.
Encryption and authentication
When the user performs the login post, from the login page, the WebMail proxy picks up the username and password and performs either of the following steps:
Proxy authentication
If proxy authentication is selected, the proxy attempts to verify the credentials through LDAP Password or LDAP Bind. If authentication fails, the login page is presented again, with the username filled-in with the same value as the user input and a message informing the user that the authentication has failed. After re-typing the password the user may request login again and the process is resumed.
Back-end authentication
If proxy authentication is disabled, the proxy looks-up the user in LDAP, identifies the back-end Axigen node, performs the authentication request and, if the authentication is successful on the back-end, provides the client with the session token and redirects it to the Inbox.
HTTP Protocol options
WebMail allows you to set HTTP limits for any request made to the WebMail Proxy service. This prevents automatically accepting excessive amounts of data (HTTP headers, HTTP body and upload data).
Instruct the WebMail service to start device detection, if a "mobile" device is detected the mobile WebMail interface will be displayed instead of the regular interface.
WebMail Proxy options
The maximum number of pending requests to each back-end can be controlled by defining the request queue size. If, for a specific back-end, a new request is incoming and the queue is at its maximum size, the "503 Service Unavailable" error is immediately returned.
Virtual host WebMail templates
The WebMail service can be configured so that each virtual host (determined by URL) is associated with a certain HSP template. All available templates are placed in a specific directory.
Thread management
The Axigen mail server is designed to run on different machine configurations and operating systems, on networks with various traffic loads, structures, domain configurations, user rights etc. That is why, depending on all these variables, you can adapt the workload to the server’s processing power to improve its performance or avoid overload by setting the minimum and maximum number of threads that can be opened at a specific moment of time.
Back-end server connection settings
In this section, you can allow a connection timeout to be set, specify the maximum number of parallel requests that can be performed on the back-end server, another local network interface IP address to be used for connections with the back-end server and whether or not to use SSL to connect to the back-end server.